The Issue
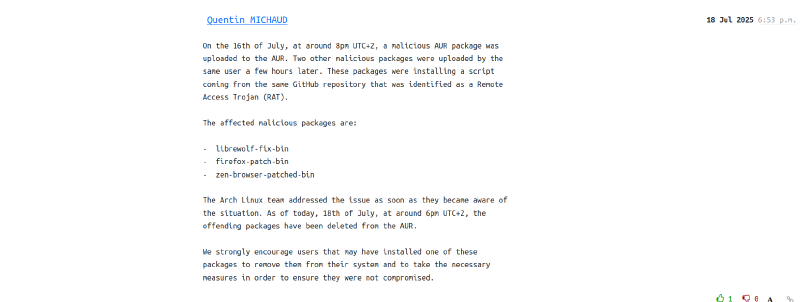
Malware-laced packages were recently uploaded to the AUR by user 🔗Quobblego
These packages have been removed, and the Arch team is aware, but to be safe, check your system to ensure you don’t have any of these installed.
Affected packages:
librewolf-fix-binfirefox-patch-binzen-browser-patched-bin
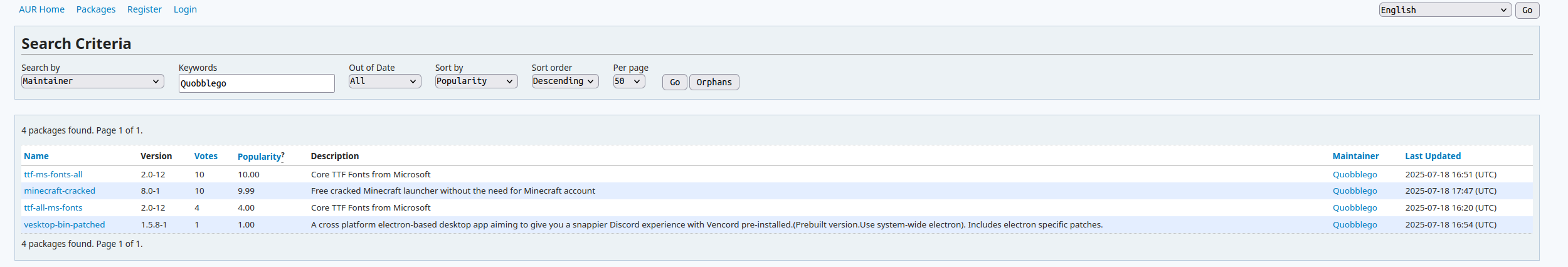
Newly identified malicious packages:
ttf-ms-fonts-allminecraft-crackedttf-all-ms-fontsvesktop-bin-patched
Source:
🔗article
Why this matters
The AUR (Arch User Repository) is community-driven. Anyone can upload packages, which means due diligence is your responsibility before installing from the AUR.
Always review PKGBUILDs, use trusted maintainers, and avoid blindly installing packages, especially -bin builds from unknown uploaders.
Honorable mention: ClamAV
🔗ClamAV ican detect some malware on-demand, but it will not protect you in real-time. Use it to scan files occasionally, but remember that your brain and good hygiene are your best security layers on Linux.
Quick check script
If you want to quickly check your system for the first three malicious packages, here’s a ready-to-use script (from CachyOS server):
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
| #!/bin/bash
#
# This script checks for the presence of specific malicious AUR packages and
# a related malicious process on Arch-based systems as per the security PSA.
#
# --- CONFIGURATION ---
readonly MALICIOUS_PACKAGES=("firefox-patch-bin" "librewolf-fix-bin" "zen-browser-patched-bin")
readonly MALICIOUS_PROCESS="systemd-initd"
# --- END CONFIGURATION ---
# --- STATE VARIABLES ---
vulnerability_found=false
found_packages=()
process_running=false
# --- END STATE VARIABLES ---
echo "🛡️ Starting security scan..."
echo "---------------------------------"
# 1. Check for malicious packages
echo "🔎 Checking for malicious packages..."
for pkg in "${MALICIOUS_PACKAGES[@]}"; do
# Use pacman -Q to query the local database. Redirect output to /dev/null.
if pacman -Q "$pkg" &> /dev/null; then
echo " [!] FOUND: Malicious package '$pkg' is installed."
found_packages+=("$pkg")
vulnerability_found=true
else
echo " [✔] OK: Package '$pkg' is not installed."
fi
done
echo "" # Newline for readability
# 2. Check for malicious process
echo "🔎 Checking for malicious process..."
# Use pgrep -x for an exact process name match.
if pgrep -x "$MALICIOUS_PROCESS" &> /dev/null; then
echo " [!] FOUND: Malicious process '$MALICIOUS_PROCESS' is running."
process_running=true
vulnerability_found=true
else
echo " [✔] OK: Process '$MALICIOUS_PROCESS' is not running."
fi
echo "---------------------------------"
echo "📊 Scan Summary"
echo "---------------------------------"
if [ "$vulnerability_found" = false ]; then
echo "✅ SYSTEM CLEAN: No malicious packages or processes were found."
else
echo "⚠️ VULNERABILITY DETECTED! Immediate action is required."
echo ""
if [ ${#found_packages[@]} -gt 0 ]; then
echo "The following malicious package(s) must be removed:"
for pkg in "${found_packages[@]}"; do
echo " - $pkg"
done
echo "➡️ Run this command to remove them:"
echo " sudo pacman -R ${found_packages[*]}"
echo ""
fi
if [ "$process_running" = true ]; then
echo "The malicious process '$MALICIOUS_PROCESS' must be stopped."
echo "➡️ Run this command to stop it:"
echo " sudo killall $MALICIOUS_PROCESS"
echo ""
fi
echo "🔒 After taking the steps above, it is strongly recommended to check for persistence mechanisms and change critical passwords."
fi
|